Vulnerability Assessments
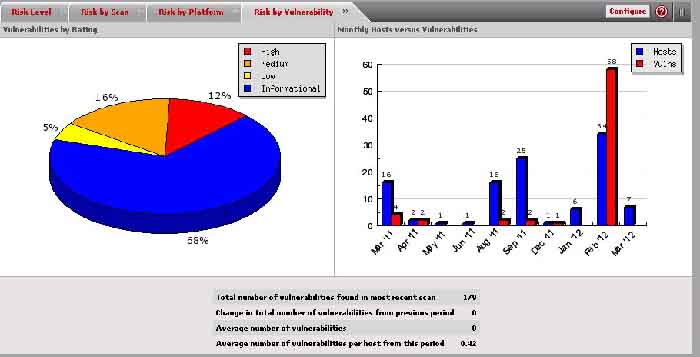
Technology is frequently mis-configured or mismanaged, which in turn introduces points of weakness into the organization. Every device connected to the network has the potential to allow an attacker in. Vulnerability assessment can be used against many different types of systems such as networked based, host based or application based. Vulnerability Assessments are necessary to identify vulnerabilities, but also are necessary to show changes in the environment over time as the organization grows and changes.